ACCESS CONTROL SYSTEM

| Access control systems are the electronic systems that are designed to control through a network and they should have an access to a network. Access Control System recognizes authenticates and authorizes entry of a person to enter into the premise thereby giving complete protection ensuring security with the system. |
 |
 |
 |
 |
|
3 TYPES OF ACCESS CONTROL: WHICH IS RIGHT FOR YOUR BUILDING? When it comes to protecting your home or business, as well as the building’s occupants, access control is one of the best ways for you to achieve peace of mind. But, access control is much more than just allowing people to access your building, access control also helps you effectively protect your data from various types of intruders and it is up to your organization’s access control policy to address which method works best for your needs. There are a number of access control systems you have to choose from to use in your residence or business facility; some outperform others. Outlined below are overviews of the three basic types of access control systems that are available to your company so you can see which are best suited for your day-to-day operations. The Three Types of Access Control Systems, In brief, access controls is used to identify an individual who does a specific job, authenticate them, and then proceed to give that individual only the key to the door or workstation that they need access to and nothing more. Access control systems come in three variations: Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role Based Access Control (RBAC). |
 |
 |
 |
|
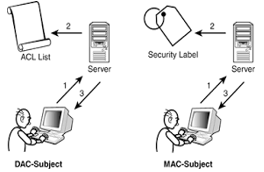
Discretionary Access Control is a type of access control system that holds the business owner responsible for deciding which people are allowed in a specific location, physically or digitally. DAC is the least restrictive compared to the other systems, as it essentially allows an individual complete control over any objects they own, as well as the programs associated with those objects. The drawback to Discretionary Access Control is the fact that it gives the end user complete control to set security level settings for other users and the permissions given to the end user are inherited into other programs they use which could potentially lead to malware being executed without the end user being aware of it. |
Mandatory Access Control is more commonly utilized in organizations that require an elevated emphasis on the confidentiality MAC doesn’t permit owners to have a say in the entities having access in a unit or facility, instead, only the owner and custodian have the management of the access controls. MAC will typically classify all end users and provide them with labels which permit them to gain access through security with established security guidelines. |
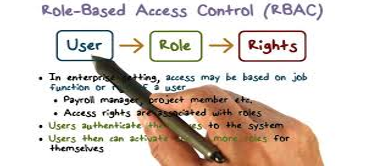
Also known as Rule-Based Access Control, RBAC is the most demanded in regard to access control systems. Not only is it in high demand among households, RBAC has also become highly sought-after in the business world. In RBAC systems, access is assigned by the system administrator and is stringently based on the subject’s role within the household or organization and most privileges are based on the limitations defined by their job responsibilities. So, rather than assigning an individual as a security manager, the security manager position already has access control permissions assigned to it. RBAC makes life much easier because rather than assigning multiple individuals particular access, the system administrator only has to assign access to specific job titles. |
 |
FACE RECOGNITION PERSONNEL ATTENDANCE CONTROL SYSTEMS |
|
Choosing the Best Access Control System for Your Organization As you can see, when it comes to choosing the type of access control system that is most suitable for your organization, there are a number of factors involved. Some of those factors include the nature of your business, security procedures within the organization, and the number of users on the system. Places of business with small or basic applications will probably find Discretionary Access Control to be less complicated and better utilized. If, however, you have highly confidential or sensitive information on your business platform, a Mandatory Access or Role-Based Access Control system are two options you may want to consider. Wasib provides the highest level of security for facilities, assets, networks and resources. Request information……… |
